Cloud Security Considerations for Small Businesses
Even though cloud adoption rates are on the rise and small business owners are not as hesitant to explore the options provided by these solutions as they once were, there is still a fair bit of confusion and misinformation floating around. One of the most commonly mentioned issues, and one of the largest deterrents to new potential adopters is the question of security of their data.
While there have been problems in the past (which is hardly surprising with any new type of technology) the issue may have been blown out of proportion by people who, perhaps, aren’t entirely competent to assess the risk levels accurately. Seeing how the best way to fight misinformation is educating people, we tried to give you as comprehensive an overview of potential cloud security issues and ways to deal with them as possible.
General Considerations and Risk Assessment
Before we dive into the more specific issues, we have to take a look at some questions that you have to ask before even deciding to move your business to the cloud. Naturally, you can’t make a completely informed decision on the risk levels before you are aware of the all the possible security issues, but there are some things that you can determine.
First of all, you have to assess how critical and sensitive the data that you are thinking about sending to the cloud is, and how much do you stand to lose should it be compromised (accessed by a third party, or simply becomes unavailable). Once you have a reasonably accurate risk assessment, leveraging the gains from moving to the cloud and fallout in the worst case scenario, you can decide if the move is justified and feasible.
Types of Deployment and Service Models
There are several specific cloud deployment and service models, all of them coming with their specific purposes, benefits and risks. While service model will be pretty much determined by your particular needs, you may have some choice on the type of deployment model that you will go with.
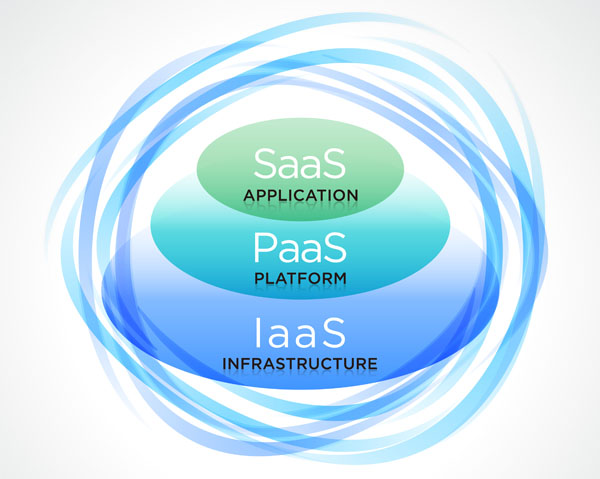
Deployment models include public, private, community and hybrid cloud systems, while most commonly used service models are Software as a Service – SaaS, Platform as a Service – PaaS, and Infrastructure as a Service – IaaS. We’ll take a quick look at each of these models, but before making your choice, you’d do well to get better acquainted with each.
Deployment Models
Public
This is the most frequently used cloud deployment model, both because of its accessibility and the greatest projected savings, and because of the fact that it is commonly used by members of the public. It includes everything from simple mail clients, to different specialised applications.
It is also the model that is the most vulnerable to intrusion and failures, due to multi-tenancy (to be better explained later on) and high number of users per vendor. While it may be the best option for a majority of small businesses, due to its flexibility, lower investment requirements and ease of transition, it does come with a limited control and lower security.
Private
Usually the most expensive and demanding deployment model, but one that affords you the greatest level of security and control over your data and the way it is handled. Private cloud can either be hosted on your own hardware or on vendor’s. Naturally, hosting it on your own servers is the safest option, but is also the priciest one, and one that will require more of your IT staff.
Even if you decide to host your private cloud on vendor’s server, you still retain an enviable amount of control. You can negotiate being the only user of the server, eliminating the multi tenancy issues; implement your own security protocols and have a greater amount of control over the ones implemented by the vendor; completely customise the cloud’s operations and protocols to fit your needs, and generally, dictate how the cloud is managed.
Community
Basically, a community cloud is a private cloud fragmented so that it includes several end users. This model is most commonly used by organisations with several branches that need some autonomy, but also want to share the cloud’s resources and setup.
If properly managed it does come with lower costs than private cloud model and greater security than public, however, most small businesses won’t have a need for this kind of model, as they would be better served by either of the previous two deployment types.
Hybrid
Usually a combination of public and private models. This means that you can use some of the resources of a public cloud, but still have your data protected in the private section of the hybrid cloud. Probably the most demanding deployment model when it comes to setup and maintenance, hybrid cloud does offer unique benefits to those willing and capable to deal with its requirements.
Service Models
The service side of the equation is key, as the higher up the model you go the more specialised the service becomes, this is explained below.
Software as a Service
The most common type of service, SaaS solutions provide users with different kinds of cloud based applications. What recommends them the most over traditional model of buying software is great flexibility and scalability, as well as the fact that they require less involvement on the user’s end when it comes to maintenance, seeing that the provider takes care of all updates and troubleshooting.
Platform as a Service
Mostly used by people wanting to host their cloud environments or develop and host cloud applications. Vendor provides the users with a platform, which includes hardware, server applications and operating system, while the user is simply in charge of the applications they upload to the cloud, or that they have developed there.
Infrastructure as a Service
This service model simply involves the vendor leasing their hardware and its resources to the end user. You are in charge of setting up the operating system as well as anything else required. This service is most commonly used by people who wish to create their own cloud (of any kind- public, private, community or hybrid), but don’t want to have to invest in the equipment.
Vendor End Considerations
While there are a number of things on your end that you need to be careful about, and we’ll consider them later, the first thing that you have to do is examine the vendor’s policies and abilities. The list is quite long, but checking each entry should give you a much better idea of what level of security and reliability you can expect. Most of the needed information will be covered in the Service Level Agreement that you will sign with the vendor, however, there are things that you’ll have to check elsewhere.
Recovery, Redundancy and Reliability
You have to have detailed information on how vendor handles critical situations, such as loss of your data. Data loss is simply something that you have to accept as a possibility, which means that you have to know how effective a vendor is at recovering it. You need to check if vendor has recovery systems in place, how effective they are, and how long are recovery processes expected to last. Likewise, you have to check how vendor prioritises in these cases. If they experience a serious failure, chances are that all of their clients will be impacted, so you need to know that you won’t be last in the line of customers they try to help.
Additionally, you have to know how fast the vendor is to respond to critical situations, and how capable they are of offering adequate, effective support. You can get fairly accurate estimates, so don’t simply take their word that they’ll provide you with a ‘timely response’. Likewise, you need to know what kind of emergencies and issues they are willing to inform you of, and how fast they are capable of doing it. This also means that it would be wise to check the level of expertise of vendor’s staff, their qualifications and experience.

Redundancy is another important aspect of every contract that you have to be completely familiar with. Basically, you have to know how protected you are from vendor’s servers overload, and where your data is kept. More reliable vendors usually spread your data over various servers, which means that you have backup in case of emergency, and that you will still be provided with the required service, even if one or several of their servers fail.
Availability
Most vendors stipulate the amount of scheduled outages and offer compensation for any unplanned problems with the availability of their services. When it comes to scheduled outages, you have to check if their duration and exact timing is permissible by your requirements. Vendors with sufficient redundancy coverage will be able to perform the needed maintenance without depriving you of service, so if you have high requirements when it comes to availability, this is definitely something to look for.
Naturally, apart from preparing yourself for scheduled outages, you have to be ready to deal with unplanned ones. Vendors will usually have a bit of breathing room when it comes to availability, meant to cover them in cases of emergencies, so you have to be fine with them being unavailable for the duration. They usually keep this allowed downtime to a minimum, and offer compensation for going over.
Naturally, you have to check if this compensation is adequate, i.e. if it at least comes close to making up for the damage you’ve suffered because of it. However, since it is usually something like offering a couple of extra hours of service free of charge, chances are that you won’t exactly be thrilled with their compensation.
Vendor’s Security Measures
There are a number of security related issues that you should get informed on prior to signing on with a vendor. First of all, you have to make sure that you know what kind of process they are using for deleting your data.
Just pushing ‘delete’ or closing the account with a provider doesn’t meant that your data is completely destroyed, so make sure to check how a vendor disposes of your data. Likewise, you should also check how easy it would be for you to get access to that data if you decide to change your vendors or if the current one goes out of business.
Vendor’s approach to security includes a number of things, including data monitoring, gateway technologies and certifications, their security posture, user authentication methods, customer segregation policies, and even their physical security policies. We’ll take a closer look at each of these aspects.
Data monitoring refers to vendor’s vigilance when it comes to watching over your data and taking note of potentially risky changes. The closer an eye they are keeping on your data, the better the chances that they will notice an attempt of intrusion in time to prevent it.
When it comes to gateway technologies and certifications, you’ll probably need some help from someone who is decently acquainted with the terminology. While they are ready to share this info with their customers, and always willing to mention the certifications that they have earned, this might not mean too much to a laymen. Gateway technologies include data diodes, antivirus software, content and traffic flow filters as well as firewalls. Look for reliable certifications, and be aware of the fact that sometimes the measures taken to ensure a greater level of security for your data could also make accessing it somewhat more difficult for you.
Security posture issue is pretty similar to gateways, you need to know what steps the vendor is taking in order to ensure the safety of your data. Apart from knowing what technologies they are using, you also need to inquire in how frequently they are updating their software and how wide a net they are casting when looking for possible exploits or system vulnerabilities. Some vendors will allow for an audit of their security posture, which, if performed by a competent expert, should reveal just how safe your data would be with them.
On the other hand, one thing that is quite easy to check, and that plays a significant role in the overall security is the type of user authentication. This basically means how easy it is for you to sign on and access your data. While a simple user authentication may be more convenient, it is also usually also easier to circumvent. User authentication is especially important for businesses that require a number of their employees to access the cloud. Some of the recommendations regarding user authentication is to keep synchronising the vendor’s user information with your active directory, as well as to request two-factor authentication.

Customer segregation basically refers to multi tenancy that we’ve mentioned before. Multi tenancy is the practice of hosting several users on the same server, and is a perfectly reasonable way of providing cloud services, however, it can be more or less secure, depending on a number of things. Since you are sharing a server with other customers, you need to understand that those on the same server with you have a somewhat better chance of getting access to your data that someone who doesn’t have any kind of access to the server.
That’s why you have to make sure that the vendor’s virtualisation methods are giving you enough of a distance from other customers. Naturally, if you want to be completely safe from intrusion by your neighbours, you can always go with a dedicated server, that will only host your account, however, this kind of solution comes with a very steep increase in price.
Finally, you also have to take a look at vendor’s security policies. When dealing with cloud technology, it might sometimes be easy to forget that there is actually a physical component to it, physical servers in physical rooms with physical doors.
The security of facilities in which servers holding your data are located is as serious a concern as the type of firewall you are using (note to vendors, firewall might be quite an effective security measure even in the non-digital world, although perhaps not an overly practical one). Those facilities receive visitors and employ people, you have to be careful about either, just like you have to be certain that the facilities are as safe from intrusion as possible.
Legal Issues
Somehow being online feels like you’ve transgressed beyond the fickle boundaries of a world governed by laws and entered a magical land where all is permitted. This is perhaps most obvious on YouTube where users feel like all that they need to do is mention Fair Use and they are allowed to do everything they want with someone else’s intellectual property. Naturally, this is not how things really work, and you have to be just as careful about laws as you usually are.
When it comes to cloud, legal issues that you have to worry about mostly revolve around data ownership and people who may have access to your data. The question of data ownership is a pretty straightforward one – do you still own your data once you upload it to the cloud, or is that ownership transferred to the vendor? If you don’t make the effort to check, you might find your data being sold by liquidators if the vendor happens to go out of business, so verify the ownership policies before signing on.
The other part of the question is not quite as simple. Chances are you’ve heard about the PRISM issue, and perhaps other similar instances of government’s unwillingness to respect people’s privacy, and this is exactly why you have to know the exact laws protecting you from government’s (or even the public’s – Freedom of Information requests and similar) prying eyes.
However, it is not only your country’s laws that you have to be familiar with, but those of all the countries that have anything to do with your vendor, or your data. This includes the vendor’s country of origin (just because they are doing business in Australia doesn’t mean that that’s where they are registered), the location of their servers, and the roads that your data travels. If your data is stored or backed up on a particular server, you need to know the laws of the country in which the server is located, and the same applies if your data is only travelling through a particular country.
Remember, vendors can be subpoenaed to share your data, and in some cases they are prohibited from informing you of this. Which is why you always have to stay vigilant, and be sure that you are informed on your rights and the exact location of your data at any time.
Doing Your Part
There are a number of things, apart from choosing the most reliable vendor and deployment model, that you can do to ensure maximum safety of your data. Before anything else this means creating a reliable backup and disaster recovery plan. Some people choose a different vendor for backup, which means going through all the same steps once again, while others prefer having their data backup offline. If you choose a different vendor, you can create a setup where the functionality is immediately transferred to them should your original vendor fail to provide you with consistent service. While this allows you to get back to work faster, it does come with risks of its own.
Likewise, you have to keep complete control over how your employees log on, what kind of network they are using, and generally, how educated they are on the possible risks. First of all, this means creating a multi-layered authentication system where the employees only have access to that data that they strictly need, nothing more. Apart from that you need to make sure that the network connection you are using to access the cloud is completely secure, and that your employees are not trying to log from a public network. Naturally, it also means having employees who you can trust won’t intentionally abuse the data that they can access.
While it is your vendor’s responsibility to monitor your data, it is yours as well. Most vendors provide you with a set of tools that you can use to check up on your data, and if they don’t, they might once you ask them. Basically, it comes down to making sure that you have the means of keeping your data safe, which is something that is vendor’s duty to provide.
Finally, you should explore different encryption options that are available. Some vendors encrypt your data, but for this to work you have to have complete trust in them and their employees, as this means that they can also decrypt it, and might be required to do so by the government.
This is to say that the safest approach is to encrypt the data yourself before sending it to the cloud. While this might make collaboration more difficult, and generally, make your data less accessible, it is the best way to ensure that no one else gets a peek at what you are trying to keep private. In the end it comes to usability VS security, which is an estimate that you’ll have to make for yourself.
Parting Words
This might seem like too much trouble just to be able to make use of cloud services without having to worry about privacy, and in most cases, it is. Most small business will never have different governments or hackers even interested in their data in the first place, while most of the reliability issues are sorted with a timely backup, but we still decided to give you a broader overview of potential issues, so that you know what your options are.
This is no place to go into all the benefits that moving your business to the cloud could provide you with, but take our word for it, most of the times, they heavily outweigh the potential risks, so if security is your main holdup with taking this step, our advice would be to ignore all the fear mongering, take the necessary precautions and dive into this beautiful world of possibilities that the cloud is building for all of us.
Resources:
- https://downloads.cloudsecurityalliance.org/initiatives/top_threats/The_Notorious_Nine_Cloud_Computing_Top_Threats_in_2013.pdf
- https://downloads.cloudsecurityalliance.org/initiatives/guidance/csaguide.v3.0.pdf
- http://privacy.org.nz/news-and-publications/guidance-notes/using-the-cloud/cloud-computing-checklist-for-small-business/
- http://www.cloudave.com/34670/top-cloud-computing-security-issues-solutions/

Pingback: What You Can Get From Outsourced IT Services - Globality Consulting()