Security Update: Bash Shellshock Vulnerability
NOTE: This article was originally published with the incorrect dates (24th June, instead of 24th September).
On the 24th September 2014 a serious Bash shell vulnerability was announced (CVE-2014-6271 / CVE-2014-7169) ). This affects most Linux operating system flavours.
This bug was code named “Shellshock” for easy reference.
Vulnerability Info
The “Shellshock” vulnerability was due to a bug in the way the common Linux software package “Bash shell” handles the execution of certain commands.
Essentially the bug could be exploited to execute code on a server with minimal access, there by compromising the server and opening the door to further attacks, exploitation or damage.
Current affected Linux distributions include:
- CentOS (5.x through to 7.x)
- Red Hat Enterprise Linux (4.x to 7.x)
- CloudLinux (All versions)
- Fedora
- Debian
- Ubuntu
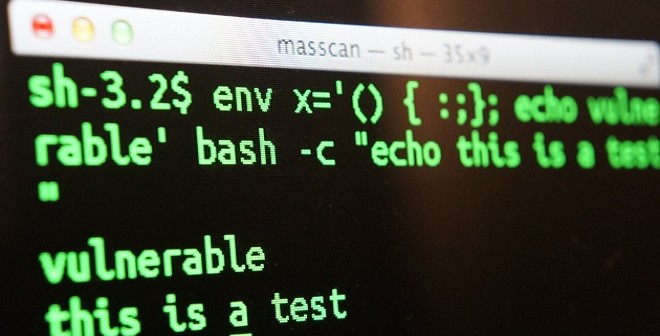
For the more technically inclined, if you want to test your system to see if you are vvulnerable to this exploit, you can run this command from the shell:
$ env x='() { :;}; echo vulnerable' bash -c "echo this is a test"
vulnerable
this is a test
In the above example you can see the word “vulnerable” was displayed after running the command. This means you are not patched.
After you have patched your system you can run the same command again, and you should get the following result,
$ env x='() { :;}; echo vulnerable' bash -c "echo this is a test"
bash: warning: x: ignoring function definition attempt
bash: error importing function definition for `x'
this is a test
In the above example you can see that an error was displayed instead of the word “vulnerable”, so this is a successfully patched system.
What We Have Done
On the 24th September 2014, we patched all core servers, including our Shared / Reseller servers. We additionally prepared, tested and rolled out the patch to our new Managed VPS offering.
Over the next few days we have been patching our non-core systems.
We prepared a KB article for our VPS or Dedicated Server customers whom wanted to patch the issue themselves.
What You Should Do
If you are a self-managed VPS / Dedicated Server customer running an affected Linux flavour we recommend you take action and patch your server immediately.
We’ve prepared a KB Article for you to follow, https://help.crucial.com.au/hc/en-gb/articles/203038994
If you are a VPS / Dedicated Server customer with the “Full Management” support option (or are on our new Control Panel VPS offering) please open a support ticket and we will check and patch as required.
If you are on a new Managed VPS offering, we have already patched you, and no further action is required.
Want To Know More
If you are interested to understand more about this exploit. Please see the following links,
-
Kyle Stevenson
-
CrucialCloudHosting
